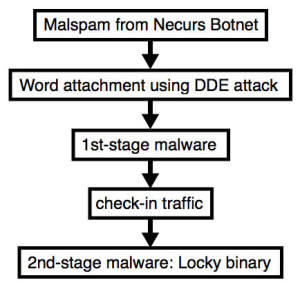
The cautious people at the Internet Storm Centre (SANS) have observed one more campaign trying to abandon the Locky ransomware utilizing cooperated Word files. As Internet Storm Center supervisor Brad Duncan states, the direction in the Word documents utilizes Microsoft Dynamic Data Exchange (DDE), a distinctive attribute that allows Office application to load data saved in a file from a different Office file. It is the sort of attack that past week was marked in a phishing campaign initiated at Freddie Mac.
The phishing announcement conveying this attack arisen from the Necurs botnet, he writes, and as with variant DDE attacks the purpose is simply to persuade the users to accept through the security alerts. A bogus invoice is the swindles’ ideal weapon. If such attack scams the target, the infected document gets a downloader which at the time pulls a print of Locky to decrypt at the object.
The minute the ransomware’s set up and it’s encrypted the target’s hard-drive, Locky is erased, leaving behind a downloader, and then claims for 0.25 Bitcoin allotted.
Duncan writes: “This is an interesting development, because it shows how the DDE attack technique has spread to large-scale distribution campaigns. It’s not new, and I’m not sure how effective it really is. If you know of anyone who was infected from one of these DDE-based Office documents, please tell your story in the comments.”
The Register distinguished past week that DDE (Dynamic Data Exchange) has been around since 1987, and it’s continuously famous aim for attackers.
Since the users have to accept implementation, Microsoft persistently determined DDE is an attribute, but not a bug at all.