Perforator tester Sabri Haddouche has reinstated the world regions to email source tricking, evading spam filters and shields like Domain based Message Authentication, Reporting and Conformance – DMARC, thus posing a hazard to anybody running a susceptible and non-fixed email customer.
What he’s discovered is that more than thirty email customers containing Apple Mail, Thunderbird, different Windows customers, Yahoo! Mail, ProtonMail and more spoiled their application of an earliest RFC, allowing an attacker scheme the software into exhibiting a fooled from field, however what the server realizes is the actual sender.
That signifies if the server is aligned to utilize DMARC, Sender Policy Framework – SPF or Domain Keys acknowledged Mail (DKIM), it will serve a message as legal, even if it should be spam-binned.
The RFC in demand is RFC 1342, “Representation of Non-ASCII Text in Internet Message Headers”, and the execution error Haddouche discovered was that email customers and Web mail interfaces do not accurately clean a non-ASCII string after they crack it.
The embedding, Haddouche wrote, can use either =?utf-8?b?[BASE-64]?= or =?utf-8?Q?[QUOTED-PRINTABLE]?= for the embedding.
Taking Apple Mail as the example, Haddouche wrote that if it’s fed the following – From: =?utf-8?b?${base64_encode(‘[email protected]’)}?==?utf-8?Q?=00?==?utf-8?b?${base64_encode(‘([email protected])’)}[email protected] – there are two security issues, namely:
- iOS has a null-byte inoculation bug, so it refuses the whole lot after that byte and appears [email protected] as the sender;
- MacOS macOS refuses the null-byte but will end after the initial effective email it realizes.
He labelled the bug “Mailsploit”, and offered a complete list of susceptible customers here.
As readers will observe perusing the list of mail apps, Mailsploit has additional nasty lateral: some concern ticketing systems (Supportsystem, osTicket and Intercom) are also matter to the bug; and in quite many mailers, the bug can also be oppressed for cross-site scripting and code inoculation occurrences.
Quite many vendors Haddouche communicated have either fixed or however got to work on a fix, but Mozilla and Opera estimate it’s a server-side issue, and Mailbird “closed the ticket without responding”.
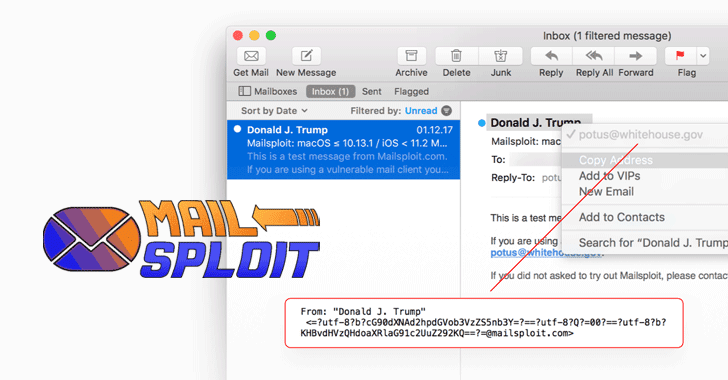 Image Source
Image Source