What is Secure Sockets Layer (SSL)?
First developed by Netscape in 1995, SSL, or Secure Sockets Layer, is an encryption-based Internet security protocol that ensures confidentiality, verification, and data integrity in Internet communications. SSL is the precursor to the contemporary TLS encryption used today.
How does SSL/TLS work?
To provide a high level of confidentiality, Secure Sockets Layer encodes data that is transmitted across the web. This means that anyone who seeks to capture this data will only see a distorted mix of characters that’s almost impossible to decrypt.
Secure Sockets Layer starts a verification process called a handshake between two communicating devices to guarantee that both devices are indeed who they claim to be. SSL also numerically signs data in order to provide data integrity, confirming that the data is not tinkered with before reaching its intended recipient.
Encryption algorithms
Generally used in computer communications, including FTP transfers, encryption algorithms are used to provide safe transfers. If an algorithm is used in a transfer, the file is first deciphered into an apparently worthless cipher text and then moved in this configuration; the receiving computer uses a key to interpret the code into its original form. Therefore, if the message or file is captured before it reaches the receiving computer it is in an impracticable (or encrypted) form.
Here are some commonly used algorithms:
DES/3DES or TripleDES
First used by the US government in the late 70s, this is an encryption algorithm called Data Encryption Standard. It is usually used in ATMs (automated teller machines) and is employed in UNIX password encryption. Triple DES or 3DES has substituted the older versions as a securer technique of encryption.
Blowfish
Unpatented and free to use, Blowfish is a symmetric block cipher, which was developed by Bruce Schneier and introduced in 1993.
AES
Advanced Encryption Standard uses the Rijndael block cipher approved by the National Institute of Standards and Technology (NIST). AES was created by cryptographers Joan Daemen and Vincent Rijmen and substituted DES as the U.S. Government encryption method in 2000.
Twofish
Unpatented and open source, Twofish is a block cipher designed by Counterpane Labs, which was one of the five Advanced Encryption Standard (AES) finalists.
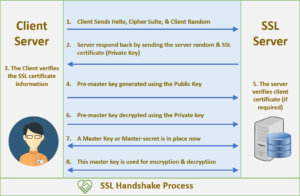
What happens in an SSL/TLS Handshake?
Every SSL/TLS connection starts with a “handshake”, the compromise between two parties that identifies the details of how they’ll progress. The handshake ascertains what cipher suite will be used to encode their communications, authenticates the server, and founds that a secure connection is in place prior to commencing the actual transfer of data. All this occurs in the background – every time you direct your browser to a safe site a complex communication occurs to ensure that your data is secure. Some misperception about how SSL/TLS handshakes work is because of the handshake being only the runup to the actual, protected session itself. Let’s try to highlight some common points:
Asymmetric vs symmetric encryption
The handshake itself uses asymmetric encryption, by making the most of two separate keys, one public and one private. Since asymmetric encryption systems have much higher cost, they are unable to provide full-time, practical security. Therefore, during the handshake only, the public key is used for encryption and the private key for decryption, which lets the two parties privately establish and exchange a newly-created “shared key”.
What is a “cipher suite”?
The handshake has many phases, each achieved according to diverse rules. The crux of it is that rather than a string of distinct to and from negotiations the parties can decide to use a “cipher suite” – a pre-existing selection or kit of agreed-upon mechanisms. TLS provisions take into account a large number of cipher suites, and the client and server will nearly always have access to one they can both hire.
Basic vs mutually-authenticated handshake
Another puzzling point is that the rudimentary model we described above allows the client to confirm the server, and the massive majority of sessions acquired by TLS only require this. Nevertheless, some cipher suites will need the client to also send a credential and public key for mutual verification of both parties. This two-way verification will certainly add expense to the handshake, but in some situations the cipher suite will want it done, and the additional security is thought worth it.
Advantages of an SSL
One advantage of using an SSL on your website is that it encodes all the information stored and used on your site. This secures card information and passwords thwarting cyberthieves from being able to steal and use the information. Another advantage of having an SSL is that it confirms your site, which tells your visitors that this is a genuine website and not a bogus one. A number of people have fallen prey to rip-offs like this, and having an SSL can reassure your visitors that the website is absolutely genuine.
Having an SSL has been verified by Google to help you rank better in search results. The Google algorithm has been tweaked to help websites that have SSL certificates; no wonder, when you look at the top results for nearly any keyword, the big majority will have an SSL.
Disadvantages of having an SSL
The key drawback is the cost of buying and setting up an SSL. An inexpensive SSL can cost as low as £30 per year and the expensive ones can cost £2,000 per year. The problem is that quality is a very important factor when it comes to these certificates because the cheapest ones are very poor and unreliable. This can then lead to further misunderstanding about where to buy the SSL from and who to trust.
Conclusion
Secure Sockets Layer is a godsend for a website that carries out online transactions or has a login page. SSL helps increase Return on Investment (ROI) of a business by winning the assurance of visitors and customers. Several attacks against SSL have zeroed in SSL execution issues, but the POODLE (Padding Oracle On Downgraded Legacy Encryption) is a known flaw in the SSL 3.0 protocol itself, misusing the way in which it disregards padding bytes when running in cipher block chaining (CBC) mode.