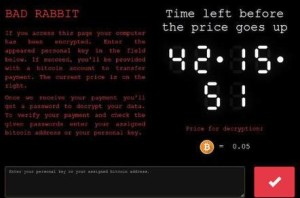
BadRabbit is a new threat – ransomware attack spreads all around Eastern Europe. It has been observed and infected all through Russian, Ukrainian, and across some Eastern European countries. It has affected the entire corporate network, computer system, Odessa International Airport – Ukraine, and numerous media outlets of Russia. The targeted locations have been are systems encrypted and all those computers’ display a specific ransom message.
Cybersecurity firm Kaspersky Lab is monitoring this unexpected malware and compared it to the WannaCry and Petya cyber-attacks that have affected a great number of government agencies and businesses; affecting mostly in Ukraine at the beginning of 2017.
While ESET has announced that BadRabbit could have been affected through drive-by download i.e. where Java-Script is added in HTML coding or a .js file. While visiting a compromised website, there appears a pop-up with an alert to update the Flash Player as a trick to download and install the malware themselves.
Once a system becomes a victim of this new ransomware, BadRabbit; automatically sends a message on the Tor browser along with a certain demand of about $275 (0.05 Bitcoins), for the decryption of the data and to provide access to the devices in exchange. According to the displaying message of BadRabbit ransom, the restoring amount will get a raise after exceeding the time limit.
Russian Interfax and Fontanka both have both been smashed by this cyber-attack, including Ukraine’s Odessa International Airport and the Kiev Metro. Moreover, the threats have been spread to Turkey and Germany as well affecting various departments. Majority of straining ransomware; BadRabbit victims are found in Russia, and the threat appears to have affected devices via Russian media organizations’ hacked websites.
However, the cyber security experts had been always advised people and organizations against paying the ransom amount to such hackers. Because there is no assurance from them that they will restore your system devices as before and remove the malware after receiving the said amount from them.