A new tip of payment card information being sold on a popular online scam marketplace advises that more than thirty million payment cards may have been affected by a malware attack and data break at Wawa convenience stores and petrol stations that was first exposed in December.
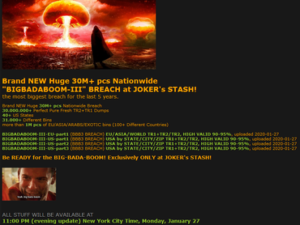
The Joker’s Stash marketplace started uploading card data Monday from a main breach called “BIGBADABOOM—III,” researchers from New York-based scam intelligence company Gemini Advisory exposed in a report.
“Gemini determined that the point of compromise for BIGBADABOOM-III is Wawa, an East Coast-based convenience store and gas station,” Gemini researchers Stas Alforov and Christopher Thomas wrote in the report, published Monday. “The company first discovered the breach on December 10, 2019.”
Joker’s Stash started promoting in December that it would upload a large assortment of U.S., European and global cards–including geolocation data listing the cardholder’s state, city, and ZIP Code–on Jan. 27. Researchers wrote that the marketplace bragged that the assortment would comprise 30 million U.S. records across more than 40 states, as well as more than 1 million global records from more than 100 different countries.
Joker’s Stash seemingly made good on its promise, but up to now only has uploaded a slice of the whole lug, according to Gemini. The middle price of U.S. payment-card records from the break is presently $17, with some of the global records valued as high as $210 per card, researchers said.
“Apart from banks with a nationwide presence, only financial institutions along the East Coast have significant exposure,” Alforov and Thomas added.
The day after Gemini issued its report, Wawa recognized that the company “became aware of reports of criminal attempts to sell some customer payment card information” from the December breach, according to a press statement.
“We have alerted our payment card processor, payment card brands and card issuers to heighten fraud monitoring activities to help further protect any customer information,” the company said. “We continue to work closely with federal law enforcement in connection with their ongoing investigation to determine the scope of the disclosure of Wawa-specific customer payment card data.”
While Wawa revealed the break in December, bad actors were gathering data for nearly 10 months using malware on Wawa’s in-store payment processing system. The malware first infected in-store payment processing systems after March 4; by April 22, most store systems—more than 850 in total—had been impacted.