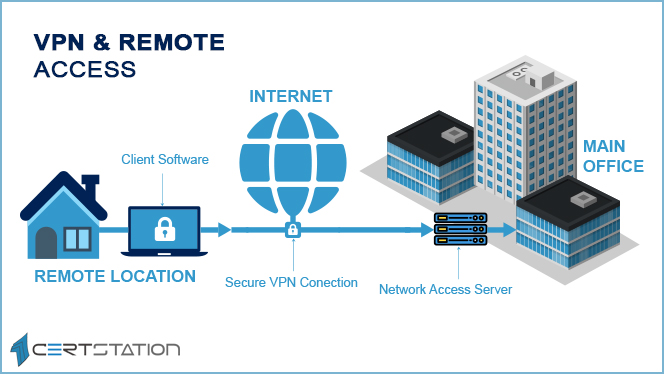
What is a VPN?
Through a VPN, or Virtual Private Network, you can create a protected connection to another network over the Web. These networks can be used to access websites restricted to specific regions, safeguard your browsing activity from snooping eyes on public Wi-Fi, and do lots of other things. VPNs today have gained traction, but they were essentially created as just a way to connect business networks together steadily over the internet or provide you access to a business network while sitting at home or anywhere you like. The VPNs basically advance all your network traffic to the network, where you can enjoy benefits like accessing local network resources remotely and avoiding Internet restriction. Simply put, a VPN provides users with a simulated network that is private so that they can connect to the internet in a safe and secure manner. Basically, the ultimate objective of a virtual private network is to ensure the confidentiality of your private information.
Types of VPN
The type of software you choose to use will determine how much or little your VPN impacts your device. Several VPNs will work straight with Windows, Mac OS, iOS, or Android, ensuring that every app that connects to the internet is safeguarded. The following are the 5 important types of VPN use for the convenience of their employees.
Standalone VPN Services
Used generally by households and small enterprises, this VPN service employs an application that produces an encoded connection to the private network that can then be utilized to connect to the Web.
Browser Extensions
Some virtual private networks serve as a browser add-on. There are a number of add-ons that can be installed to browsers like Google Chrome. The disadvantage of this is that your data will only be saved when you’re explicitly using that browser. Other apps will not be safeguarded. Also, browser virtual private networks are slightly more susceptible and IP leaks can happen. If you do choose to go for a browser add-on or extension, you should employ the services of well-known companies that offer other VPN services as well. There are many unreliable and phony browser add-ons on the market, so avoid falling into wrong hands by doing proper research and going for the appropriate VPN service.
Router VPN
Another way to enforce a virtual private network is through a VPN-enabled router. This is perfect if you have numerous devices you want to defend as it will shield every device linked to the router, saving you the hassle of installing the VPN individually. Also, signing in only a one-time activity, as your router will always be connected to your network.
If you think it’s difficult to connect your router to a VPN, you are wrong. All you need to do is sign up for a VPN service; then you’ll need a router. You should always opt for the type of router that is developed to support virtual private networks straight away, ones that keep you from the hassle of entering technical details. Although these routers can be costlier than regular ones, you should keep the factor of ease and convenience into account.
Corporate VPN
A remote-access VPN is often used by organizations to facilitate employees who choose to work from home. This VPN helps employees easily and safely access the organization’s private intranet, mostly by using a password and an app.
What are VPN Protocols?
VPN protocols ascertain precisely how data is routed through a linking. These protocols have diverse stipulations based on the advantages and anticipated conditions.
PPTP
This is one of the oldest VPN protocols which was developed in the mid-90s by software giant Microsoft. PPTP was combined into Windows 95 and precisely intended for dial-up connections. But as technology developed, this protocol’s basic encryption was swiftly fractured, compromising its fundamental security. Nevertheless, since it doesn’t have many of the security features found in other modern protocols, it can provide the best connection speeds for users who may not need hefty encryption.
L2TP/IPSec
A substitute for the PPTP VPN protocol, L2TP doesn’t provide any encryption or privacy and is often coupled with security protocol IPsec. Once applied, this protocal is highly secure with virtually no flaws.
OpenVPN
This protocol allows developers to access its fundamental code. OpenVPN has become hugely popular because of its use of AES-256-bit key encryption with 2048-bit RSA verification and a 160-bit SHA1 hash algorithm.
SSTP
Secure Socket Tunneling Protocol is extensively used owing to its full incorporation with every Microsoft operating system. SSTP exploits 2048-bit SSL/TLS certificates for verification and 256-bit SSL keys for encryption. The major disadvantage to SSTP is that is essentially a Microsoft-developed proprietary protocol and developers do not have access to the fundamental code.
IKEv2
It’s is a common VPN tunneling protocol that offers a safe key exchange session. Similar to L2TP, IKEv2 is usually coupled with IPsec for encryption and verification. This protocol is excellent at reconnecting the link after brief connection loss and shines at swapping connections across network types.
Conclusion
A modern internet user cannot deny the importance and utility of a virtual private network in today’s volatile work environment. The best thing about a good VPN is that it ensures the privacy of your internet activity, helping prevent websites from stalking as you navigate the web. What’s more, a VPN can unclog many streaming services by letting you hide your place so you appear to be in a different country. It’s also a strong anti-censorship instrument for those who need it. Furthermore, a VPN encrypts all the data between your device and the VPN server since it is possible for cybercriminals, or the companies who run the WiFi network, to access user data when they are surfing on a public network. This saves you from anyone looking at your data through public WiFi.




