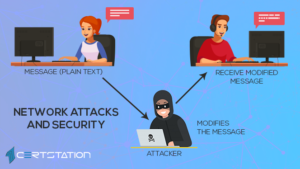
A security team comprises a group of people who are committed to and responsible for evaluating any safety risks or security fears that could impact their organization, staff, and/or clients. Responsible for detecting, examining, and responding to incidents, they may also be involved in planning and executing preemptive security measures and in building disaster recovery plans.
Description of tasks matters in any organization, and it’s particularly important to make sure security incidents don’t fall through the cracks and that your complete posture is strategic and hands-on. One of the best ways to ensure that your people, procedures, and tools are all in sync, like a well-oiled machine, is to execute security automation and orchestration. It can take the pressure off numerous roles on the security team and help everyone work better in a team.
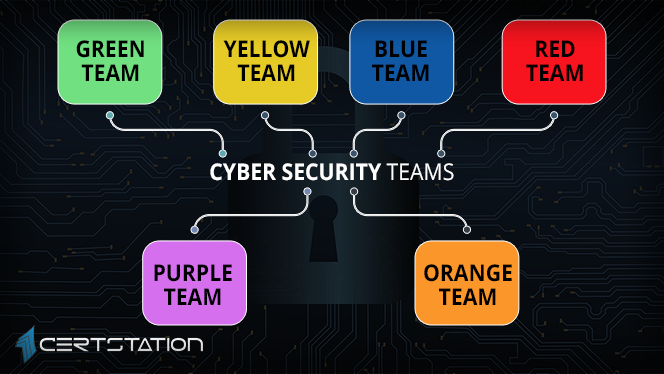
Blue team and its objective
A blue team is a group of people who carry out an assessment of information systems to ensure security, recognize security faults, authenticate the efficiency of all security measures, and to ensure all security measures will remain equally effective after implementation. Blue Teams engage an extensive range of tools allowing them to detect an attack, collect scientific data, carry out data scrutiny and make changes to threat future attacks and alleviate threats. Some of the tools include Graylog, LogRhythm, NetWitness, FortiSIEM (a.k.a. AccelOps), AlienVault, Splunk, Rapid7, and more.
The blue team is responsible for detecting and deactivating the more sophisticated attacks and thoroughly monitoring existing and developing threats to preventively defend the organization. The team’s objectives include comprehending every phase of an event and replying suitably, while observing wary traffic patterns and recognizing Incident of compromise. Swiftly closing any method of compromise and identifying the red team command and control servers and obstructing their connectivity to the target are also what blue teams do. In addition, blue team is also responsible for performing examination and forensic testing on the different operating systems their organization works on.
Red team and its objective
A red team is a group that helps companies to improve themselves by providing offensive approach to the standpoint of the company that they are helping. They are often effective in helping organizations get over cultural prejudice and widen their problem-solving abilities. Private business, particularly those deeply invested as government workers, and US government agencies such as the CIA, have long used Red Teams.
The objective of a red team test is to gain an accurate idea of the level of risk and susceptibilities against your technology, people and physical assets.
Red Teaming assessment
It is an object-oriented adversarial activity that needs a comprehensive, all-inclusive assessment of the organization from the viewpoint of a rival. The objective of carrying out a red teaming assessment is to reveal how everyday attackers can combine apparently disparate exploits to attain their objective. It is a remarkable way to show that even the classiest firewall in the world means very little if a hacker can leave the data center with an unencrypted hard drive. Rather than depending on a single network appliance to gain sensitive data, it’s better to take in-depth approach and incessantly improve your people, process, and technology.
Purple team and its objective
It is a role intended to augment the information sharing between and the definitive efficacy of an organization’s Red and Blue teams. The Purple Team is essentially a function that improves current Red and Blue abilities. Purple Teaming is high-level security designed for companies with a developed information security program. The objective is to display how susceptibilities are used against a particular configuration or situation, and whether they are noticeable. Purple Team is also supposed to make best use of the results of Red Team engagements and improve Blue Team competence.
Yellow Team and its objective
Application designers, software developers and engineers fall into the security Yellow team. These are the professionals responsible for building and designing software, systems, and integrations that add to the efficiency of businesses and large organizations. They are mainly focused on requirements, functionality, user experience and back-end performance. Well-versed in setting up systems and code, the team’s ultimate objective is to enhance code-based and design-based defence competence for finding, incident response and data forensics.
Green Team and its objective
Well-conversant with setting up systems and code, Green Team comprises continuing organized connections between the Blue Team and members of the Yellow Team. The ultimate objective is to improve code-based and design-based defence competence for recognition, event response and data forensics. They also work together with Blue Team or Purple Team and discuss solutions and enhancements for a number of features such as DFIR Output, Logging Improvements, change management and so on.
Orange Team Inspires coders with attackers
Malicious programmers are not the reason for numerous security bugs within software; however, a dearth of security awareness within software development teams and architects does exist. The objective of the Orange Team is to stimulate Yellow Team to be more security cognizant, raising their security awareness by providing education to help software code and design execution. There should be organized and continuing engagements between Red and Yellow Team for the benefit of Yellow.
Traits of good security teams
1. They always invest in cutting-edge technology
Security companies often take technology for granted, with many thinking it’s waste of money. That’s precisely why they often get attacked, and are ultimately forced to close down. In spite of heavy investment, companies often learn about security incidents long after they occur and then scramble to fix the problem after data has been exfiltrated.
Worse, post-breach examination generally exposes warning signs that were ignored. The best security teams take advantage of advanced technology to become more practical in making risk management decisions, using technology to integrate data from across the company, so analysts can make better decisions.
2. They Appreciate What Ought to be Protected
When targeting a company, attackers have a nefarious objective in mind. Successful teams tend to think from an attacker’s perspective, and realize how technical equipment and every piece of technology relates to this objective, which may endanger their respective organizations.
Cyberthieves spend an excessive amount of time learning their targets and setup, looking for flaws and reconsidering the environment every step of the way. Understanding these designs is key to protecting against the attacks. One just can’t defend everything all the time; a great team always prioritizes assets that are most important to the organization.
3. They Realize That Alerts Shouldn’t be Relied on
Professional security teams barely respond to security alerts; they rather use them as another data theme in the risk evaluation that describes their priorities. Going after every alert offers a direct line of fiasco for security teams, creating disorder and work without improving enterprise security. The best security teams take into account alert severity in context, with aspects such as what’s being attacked and the probability of effect to the organization caused by the activity. The best security teams prioritize the events that could cause the most damage.
4. They Learn from Their Mistakes
Highly effective teams learn from their mistakes to ensure a better work environment in the future. Although cyberthieves will enhance their malware and tools, their tactics remain mostly the same. In addition to looking for malware, professional security teams look for activities that are irregular and don’t belong.
Conclusion
Security needs smart people, procedures, and cutting-edge technology. More often than not, the “people” part of the PPT equation is either ignored or given little importance. Global expenditure on digital transformation technologies is likely to reach closely $1.3 trillion in 2020, as per an estimate. But protecting against today’s threats needs more than just technology solutions — it demands a robust security team. Some of the world’s most successful organizations virtually spend millions of dollars to ensure cybersecurity and to thwart any possible attack.
As the job of protecting the organization continues to grow, security teams must also grow, both in terms of infrastructure and making their systems more reliable and effective. With an anticipated cybersecurity job scarcity of 3.5 million by 2021, it is critical now more than ever that security teams create a repeatable process rhythm that drives constancy and gives them the best shot at defending their organizations effectively. Literally thousands of hours have been spent talking to scores of security teams and the experts within an organization. What brought to light was the learning that the most successful teams implement behaviors like the ones above to confirm all members are as effective at doing their job as possible.
In the aforementioned article, we have discussed in detail what constitutes a strong security team. If you’ve had a malware infection or some other security crack, you might think yours missed the mark. Nevertheless, the examination of a team goes beyond a single incident.