What is Intrusion Detection System?
Keeping your network secure from invasion is a very important component of system and network administration and safety. If your network is infiltrated by a nefarious attacker, it can result in huge losses for your company, including likely downtime, data breaks, and loss of customer confidence. An intrusion detection system (IDS) is a means or software that functions with your network to keep it safe when somebody attempts to penetrate your system. A wide range of intrusion detection systems and plentiful tools are available on the market and it’s quite challenging to determine which one to use.
Although IDS’s screen networks for possibly malevolent activity, they are also prone to false alarms. Therefore, companies ought to modify their IDS products when they first install them. It means appropriately establishing the IDS’s to identify what normal traffic on the network looks like as compared to malevolent activity. IDS’s also supervise network packets built in the system to see the malicious activities involved in it and at the same time sends the warning alerts.
What Is Intrusion Prevention System and How Does It Work?
An IPS is a network security/threat preclusion technology that scrutinizes network traffic movements to diagnose and avoid susceptibility activities. Vulnerability activities typically come in the form of malicious efforts to a target application or service that invaders use to interject and gain control of an application or machine. After a successful exploit, the invader can incapacitate the target application, or can possibly access to all the rights and authorizations available to the compromised application.
How Do Intrusion Prevention Systems Work?
Often existing behind the firewall, the Intrusion Prevention System delivers a corresponding layer of evaluation that undesirably opts for hazardous content. As opposed to its precursor, the Intrusion Prevention System actively evaluates and takes automated movements on all traffic flows that get into the network. These actions essentially include sending an alert to the administrator, dropping the malevolent packets, clogging traffic from the source address, and resetting the connection.
As an inline security element, the IPS must work competently to avoid debasing network performance. It must also function swiftly because exploits can occur in near real-time. The IPS must also spot and respond precisely, so as to remove threats and incorrect positives. IPS’s have several ways of spotting malevolent activity, but the two major procedures are signature-based detection and statistical anomaly-based detection. The signature-based detection technique used by IPS’s includes a dictionary of distinctively recognizable signatures situated in the code of each exploit.
The Differences Between IDS and IPS
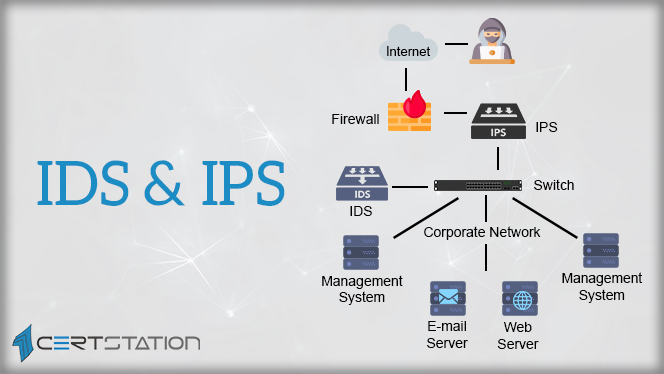
Although there are many differences between Intrusion Detection Systems and Intrusion Prevention System, the key difference between them is that IDS is a monitoring system, while IPS is a control system.
A detection system doesn’t change the network packets in any way, while IPS prevents the packet from delivery on the basis of the insides of the packet, just as how a firewall averts traffic by IP address. Intrusion Detection Systems examine and screen network traffic for indications that specify intruders are using a recognized cyberthreat to penetrate or snip information from your network. Intrusion Detection Systems liken the existing network movement to a recognized threat catalogue to spot numerous kinds of performances like security policy defilements, malware, and port scanners.
Intrusion Prevention Systems reside in the same range of the network as a firewall, between the external world and the internal network. These systems clearly repudiate network traffic based on a security contour if that packet signifies a recognized security threat. Several IDS/IPS vendors have combined newer IPS systems with firewalls to generate a Unified Threat Management (UTM) expertise that combines the functionality of those two parallel systems into a single element.
Why IDS and IPS are Important for Cybersecurity
Security firms encounter an ever-increasing threat of data breaks and compliance fines while constantly struggling with budget constraints and business politics. IDS/IPS technology protects precise and significant jobs of a cybersecurity plan. IDS/IPS systems are mostly detached, which makes them perfect contenders for use in the existing security mass. IPS delivers the peace of mind that the network is safeguarded from recognized threats with inadequate resource necessities.
In addition, part of compliance often necessitates showing that you have invested in technologies and systems to guard data. Executing an IDS/IPS solution examines a box on the compliance sheet and highlights a number of the CIS Security controls. More prominently, the checking data is a respected part of compliance investigations. As for policy enforcements, IDS/IPS are configurable to help implement internal security rules at the network level. For instance, if you only support one VPN, you can use the IPS to clog other VPN traffic. While network security is key to safety from data breaks — and IDS/IPS solutions perform that role flawlessly — real-time activity is constantly monitored on data, which is an important layer to any cybersecurity policy.
When a new ransomware attack erupts, the IDS/IPS might not have the signatures equipped to thwart the attack at the network level.
Conclusion
Intrusion detection system investigates network information flow and determines warnings when malevolent activity is conducted. They can send special messages to rearrange TCP connections after the outbreak begins, and some can even link with the firewall system, and redraft the firewall rule set online. The restraint of an intrusion detection system is that it cannot retaliate network attacks, for IDS sensors based on packet sniffer technology can only view the network information flow. IPS can carry out the same scrutiny of IDS, because they can be plugged into the network, fixed between network mechanisms, and they can stop nefarious activity. This is the biggest difference between IDS and IPS, and how to use it is of great importance. Integrating the detailed analysis and recognizing capabilities of an intrusion detection system with the stalling and defense potential of IPSs will, in experts’ view, be a very important objective for cybersecurity learners to actually understand how both systems function keeping in mind the intricacies of the technology-driven world.




