A flaw in the Linux sudo command has been exposed that could let unprivileged users perform commands as root. However, this flaw only works in non-standard configurations with most Linux servers having had no impact.
Before we get to the susceptibility, it is key to have some rudimentary information on how the sudo command works and how it can be configured.
When performing commands on a Linux operating system, unprivileged users can use the sudo (super user do) command to perform commands as root so long as they have been allowed or know the root user’s password.
The sudo command can also be configured to let a user run commands as another user by adding special directives to the /etc/sudoers configuration file.
Tracked as CVE-2019-14287, the flaw was discovered by Joe Vennix of Apple Information Security. This is cause for worry since the sudo utility has been intended to allow users to use their own login password to perform commands as a different user without the need for their password.
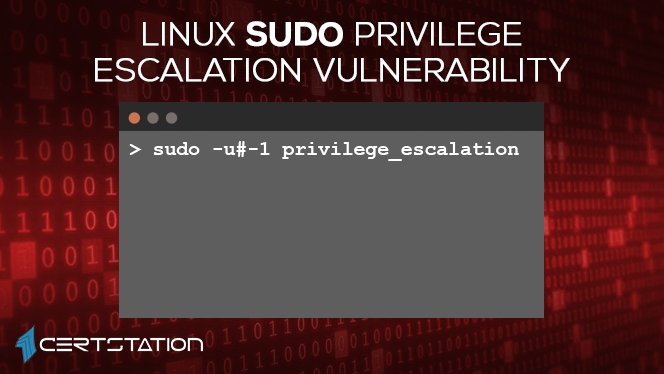
What’s more exciting is that this flaw can be abused by an attacker to run commands as root just by stipulating the user ID “-1” or “4294967295.”
That’s because the function which translates user id into its username erroneously treats -1, or its unidentified equivalent 4294967295, as 0, which is invariably the user ID of root user.
The flaw impacts all Sudo versions before the latest released version 1.8.28, which has been issued a few hours ago and would soon be launched as an update by various Linux distributions to their users.



